Time to Check with Your EDR Vendor
This month (January 2022), a team of researchers at the University of Piraeus, working in the informatics department, devised, and ran a series of tests to determine the state of Endpoint Detection/Response (EDR) systems as a follow up to a previously released paper. The researchers chose four attack methods that are found in the “wild,” meaning those that are currently being used by attackers. Because most intrusions start with a spear phishing attack where a user is lured to click on a malicious payload attached to an E-mail, the researchers chose this as their attack vector. This is quite common and the EDR should check the payload to block it before it can do harm, or at the very least, recognize the system has been comprised and report it.
The four vectors were
- An executable DLL in a Control Panel applet, commonly known as a “cpl” file. This does not look like an executable but is loaded and run by a delegate to try to hide it from the EDR client.
- A DLL that a MS Teams installation will load. The code will use a self-injection technique using an offensive toolkit called AQUARMOURY Brownie. This allows the malicious code to be executed in the address space of a “trusted” executable which means the EDR system may not see it.
- A PE EXE file that uses another technique in the AQUARMOURY toolkit called “Early Bird” to inject the malicious process in an evasive method.
- An HTA file which is a type of file that is a collection of code (hypertext, VBScript, JScript) that is run as part of a web page (or as an E-mail attachment) and executed by the Microsoft HTML Application Host (mshta.exe). This is yet another technique of code injection where trusted address space is used to hide execution from an EDR.
Again, these techniques are all common in toolkits (such as AQUARMOURY) to evade EDR detection. Since they are well known they should be detected by EDR vendors that are maintaining their code base to counter modern techniques. The results are quite telling.
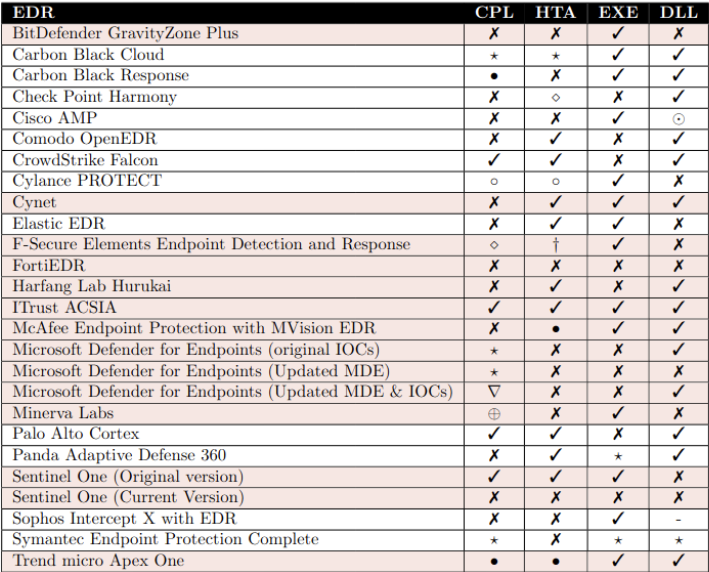

Source: “An Empirical Assessment of Endpoint Security Systems Against Advanced Persistent Threats Attack Vectors”
In the far-left column is the product being tested which includes both EDR and EDP systems. The next four columns show each of the attack vectors chosen for the study. An X indicates the attack failed and that alerts were raised. A checkmark indicates the attack was successful without any alert raised. All vendors but two allowed the malicious code to execute in one or more of the attack vectors. Only one allowed all four vectors to work while most of the others allowed at least one, with the majority being two or more. Only FortiEDR and Sentinel One (all features turned on) stopped all four attacks.
After the initial test, the researchers used what they had learned to try to disable EDR clients. These techniques included unlinking client callback functions, manually patching vector tables or functions used to gather telemetry or using known vulnerabilities to disable or kill the EDR client. Once again, these techniques used known methods and offensive toolkits already available. The extended research was able to disable or kill MS Defender for Endpoints, Sophos Intercept X, Bitdefender, and FortiEDR. Since FortiEDR was one of the two systems that detected all attacks, but could be disabled by a kill technique, only Sentinel One survived intact without any fails, provided all features are enabled.
With these results in hand, you should check with your vendor to determine what steps they have taken to mitigate these attacks. As with all security layers, nothing is hack proof. The strength of a security system is its well-chosen layers of defense to work together to defend a system instead of relying on a single element. However, this does show a difference in the quality of EDR systems now. As companies respond these results will change but, in the end, it shows what all security researchers know: techniques exist to evade tools trying to find them. It is in the holistic security system layers that real security exists.
Questions? Please feel free to contact me about these results or a review of your own security defensive posture. View the research paper.

