The Biggest Security Mistake – Part 1
The Biggest Security Mistake
You Are Making Right Now
Part 1
In this world of information security where new vulnerabilities in applications and operating systems show up daily and major breaches are announced weekly, the biggest security mistake is also one of the oldest: passwords. The idea of a password is very simple. It is something that you know that others don’t that can be used to recognize you. Even the word itself comes from its historic usage, if you know the secret word you may pass–you are one of us. A word becomes your identity even if you are unknown. Most people will immediately assume the mistake is not in picking a good one. That is a problem within itself, but that is not the biggest mistake you are making. This problem might be more about your personal passwords, but for most it also involves work passwords. Before we go forward let’s first understand exactly how passwords are used to identify you in terms of information security and the failures of the system.
The Hash
I have heard cyber-security specialists say, “I was able to retrieve your encrypted password.” This is not correct. Encryption is a two-way process where something you wish to remain secret is changed to be unusable in such a way that, with the correct key, it can be changed back to its original state.This is why it is a two-way process. Plain text (the unmodified input, called the crib) is encrypted with a key that “scrambles” it (called the ciphertext), which makes it unreadable so it can be sent over a public medium, and the receiver can supply the key to decrypt it and restore it to the original plain text.
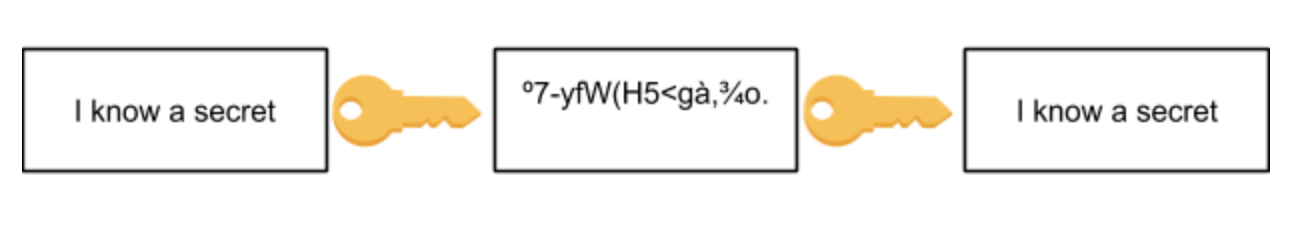
A hash is a one-way conversion from the original data to a fixed-size representation. Once converted the hash cannot be used to derive the original data. This is a one-way map that converts the data into a representation that can be used to find it again quickly (such as in hash tables.) You might think of it like a fingerprint for data. Of course, you can’t expect to represent 10MB of data using only four bytes without having collisions (where two different inputs equals the same hash) but for smaller sized inputs, such as your 32-character password, collisions are rare with a good hash function. Common hash functions you might have heard of are MD (Merkle–Damgård or Message Digest), SHA (secure hash algorithm), and BLAKE. How can a one-way function that reduces the input data to a much smaller output be useful?
We’ll use a simple hash function to store a library of books in a way to make them easy to find. Here’s a list of books:
The Cuckoo's Egg - Clifford Stoll
Sandworm - Andy Greenberg
Dark Territory - Fred Kaplan
See No Evil - Robert Baer
We’ll put the name of the book and author separated by a dash (just as above) through a hash function to get the following results (Online hash calculator – Online tools):
The Cuckoo's Egg - Clifford Stoll = 74f26962de8d5748d77a0a7b03be2153
Sandworm - Andy Greenberg = b1a7219ac45be9cd4375f6bec16b018a
Dark Territory - Fred Kaplan = 660067ecb503cc4b97801a1341197578
See No Evil - Robert Baer = 5e492f2e663023d28abacd4d2a6534df
The hash function (MD5) converted the title and author into a unique 16-byte number (displayed in hexadecimal.) Now I simply need to label my bookshelves with the first letter of the hash 0-3, 4-7, 8-b, and c-f and start putting my books on the correct shelves in alphabetic order of the hash not the title. Now to find a book, simply hash the title, dash, author and I’ll know exactly where to look. Perhaps if we did this with the whole text of the book, we might disrupt the firmly entrenched Dewey Decimal system, but this does illustrate how a one-way hash is useful.
Passwords are a type of plain text. You know your password, if you write it down on a sticky note and place it on the underside of your keyboard it is readable to all. Instead, if you encrypted it using something like 3DES Encryption and then wrote it down, no one would know your password even when they found your secret sticky note. But you’d still need to remember the password you used to encrypt it, so you’d only be exchanging one password for another. Instead passwords are hashed, and the hashes are written to a file on permanent storage. This is how computers store passwords (or should even though many times they don’t, including three FAANG companies.) In this way, even if the file is found, the passwords aren’t visible. But if the hash is one-way how do we use it to store a password?
Many people believe the password is encrypted and the encrypted version is stored. When you enter your password, the computer decrypts the one in storage and compares it to the password entered. This would allow system administrators (or hackers) to easily decrypt passwords since some master key must exist in order to decrypt the stored password. If something is stored in a computer anywhere, it is fair game for hackers. Instead, when you first enter your password, it is hashed with a hash function and the hash is written to storage in a file or database that also contains a username or user number. Then when you subsequently enter your password, the password you enter is hashed, and the hash is compared to the stored one. If they match, then you have entered the correct password, since any different password would create a different hash as each unique input text produces a unique hash.
Now that we understand what hashes are, next we’ll discuss the methods used to break them.




