The Biggest Security Mistake – Part 3
In the age of fast computers that can check tens of millions of passwords per second, are passwords even useful? The answer is yes but not the way you are using them. The mistake you are making every day is not changing them often enough and not having enough of them. You are probably also guilty of using ones that can be cracked, but it is the age of the password that determines its strength more than its complexity. If you combine a few short words with numbers and special characters such as 9Dogsclimb^ (“9 Dogs climb up”), 3boyS&6[Men] (“3 boys and 6 boxed men”) or Some1@luNch8 (“someone at lunch ate“) you have a pretty god password. Better is a phrase to a password, such as “I Never Knew How to Play the Bass Guitar” could become iNk!hTP&tBg* which is the first letter of each word in the phrase, grouped into threes with the middle letter being capitalized and each group of three followed by a special character (easier to remember than you think). These passwords are tough and short of being in plain text at the time of disclosure, will need some cracking time, except you are still at the mercy of the application builders to do a good job of using salted passwords and storing them intelligently.
However, as soon as you use the same password on another site, you have made your big mistake. No matter how good it is, you just lessened the protection it can provide you. As already discussed, companies don’t implement passwords properly in most cases. This means system administrators have access to them. If they are stored in plain text even developers have access to them. If the company is hacked and the passwords are stolen (hashed or not) your password becomes like cash on the dark web. It is used for trading, stored in databases for sale and trade, and used to try to extort money from companies.
For this article I asked for volunteers to talk to me about their password habits. I spoke to only 13 people, but I soon found that was enough. All of them used no more than about five passwords but most only three. When I asked for how many different websites, they said they didn’t really know. Most of them had a single password they used for all sites they felt were “unimportant,” such as support forums, newspapers, or anything that requires a login and didn’t have a cost. Several said they used this password because they only visited the site a few times a year and this way they always knew the password. This prompted me to ask how many times they have changed that password. The answer is, never because that would defeat the purpose of it. The second category was work. The second was their password for work. They all had another password for it, but they used it everywhere for work, giving them a single password for work. Third was their password for their banking which was their most difficult password, but they used it for all their banks and financial institutions including their credit card companies. Only 5 of the 13 people had more than 3 passwords. Three of these five had a separate password they used for their content devices like streaming TVs (such things as Netflix, Sling, Hulu). The last two used a different password for a few other sites, one because he was required to have a separate password for his VPN at work. The last remaining password for the second person with five was reserved for all medical sites.
I dug a little deeper and found one very disturbing fact. Many used their hard “bank” password for large online shopping sites like Amazon. When I asked if they had the same password for their credit card bank, their cash account bank (where their paycheck was deposited), and Amazon, 7 of the 13 said it was the same password. This means with that password, it is possible to order on Amazon, pick a new shipping address, login into the credit card site, and the bank site to pay the bill. I then asked them which password they used for their personal Email and 6 of the 13 said it was the same one as used on Amazon and their banks. This means someone can then use the same password to delete any mail that Amazon sends regarding order status and delivery, or even add filters to delete them upon receipt. The truth would only be discovered when you balance your bank account. You do do that?
In fact, the recent problems with Ring security systems was this exact problem. When signing up for Ring, people used the same password they have used for other sites for many years. Since companies have been compromised, those hashes and passwords were already posted, and they have never started using a different password, it was easy for the hackers to gain access to the Ring accounts used for the cameras. Ring stated it was a user problem, and it was, but they also, at the time, provided no better solution. However, the media coverage of the Ring incidents did highlight the problems with using a shared password over multiple applications and websites.
The biggest mistake in security you are making right now is not changing your passwords. Passwords can be very secure provided they are complex and changed often. Obviously, the last key is to use a different password for every site. This sounds hard, but in reality, it isn’t. With some simple tools you already have and a few techniques you can solve this problem right now. But it all starts with changing your passwords regularly for sites you use regularly and using a different password for every site. Fortunately, your browser can help you with this because they can remember passwords for you by storing them. They will, in fact, store those passwords on a remote server so you can use them on all your devices. This does mean if someone hacks the system containing your password database, the hacker gets them all since they are remote. For this reason, you should never store your highly sensitive passwords such as financial, banking, or medical sites in the browser. When it asks if you want the browser to remember the password choose “Never.” If the browser already has stored these passwords, you first need to check what your browser knows.
Audit your Passwords
Check the list of passwords stored in your browser. This is different for each browser but Chrome, Safari, and Firefox all have the option; for other browsers you’ll need to find this on your own.
Chrome – Chrome stores the passwords remotely on the Google servers. Click on the three vertical dots in the top right of the window
Choose “Settings” and enter “password” into the search box. Below will appear a line with a gray key followed by “Passwords.” Click on that and then choose “View and manage saved passwords in your Google Account.” It will then go to Google Servers, grab your passwords and display them.
Safari – Click Preferences.
Select “Passwords” and Safari will display stored passwords
Firefox – Click on the three verticals lines in the upper right corner.
Choose “Logins and Passwords.” All your password swill be displayed in a list on the left.
Some browsers will require you to re-enter your password or fingerprint. The list shows all the sites for which the browser has stored the password. Take some time to look through them and decide if you really need them. Some of these might be for old services you no longer use or even companies that no longer exist. Clean it up first by deleting them. For any you’re not really sure, leave them for now. You need to change them later anyway. To see the password, you might need to click on an icon (often an eye) and enter your password. Take some time and clean this list up. Delete all passwords for all sites you don’t know.
If you are using Google Chrome, on the main password management page there is a link labeled “Check Passwords.” Click on this link and Google will tell you how reused passwords you have (same password on different sites), which are known to be compromised, and how many of those are weak. For most people, it looks like this:
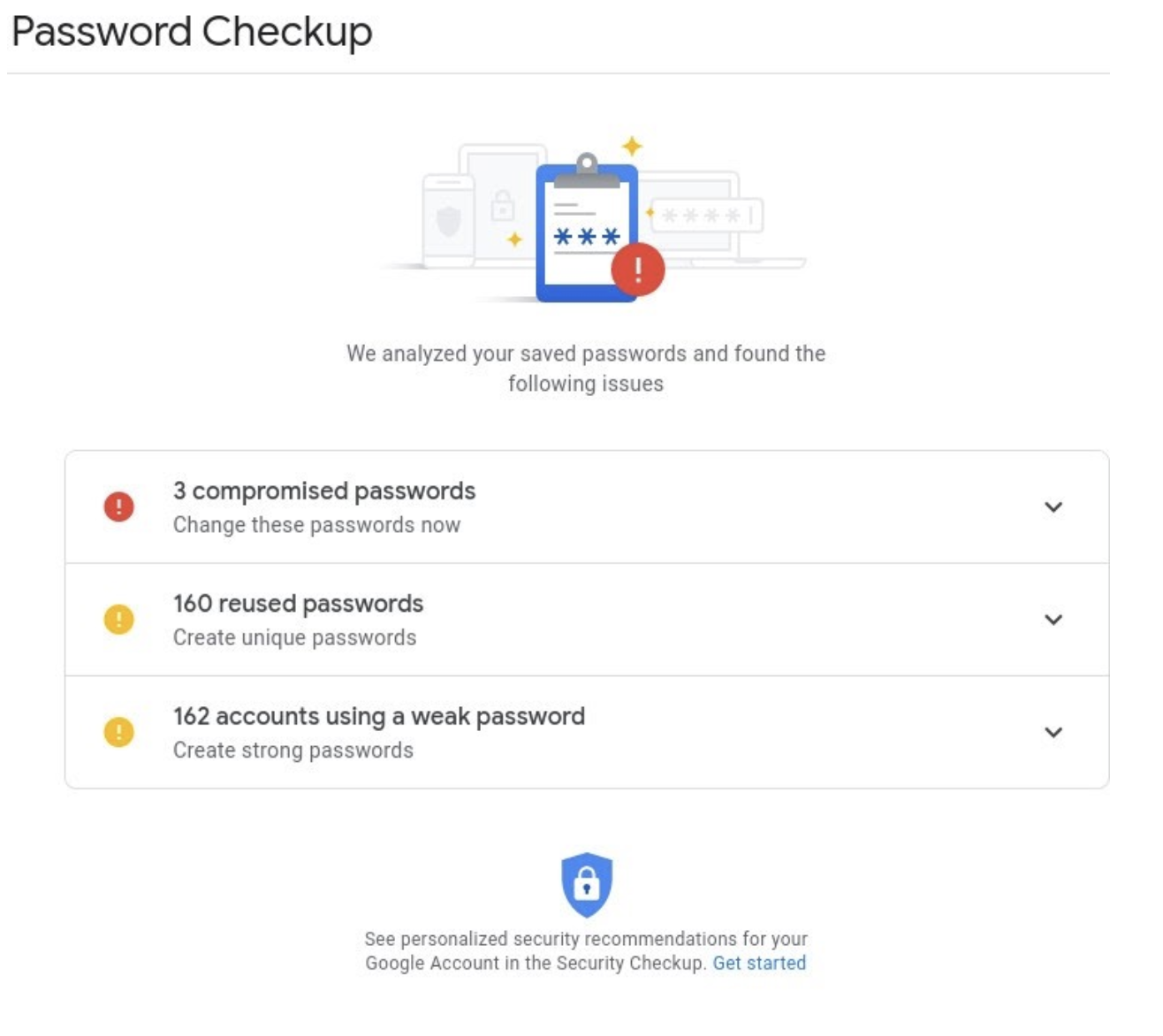
If the compromised passwords are also in the reused list, then you need to change all of them immediately. While this is a nice feature, it only works because your passwords are stored in the Google cloud on many different servers, a bad place for your passwords to reside (anywhere on any computer.) Next time we’ll look at how to properly use passwords in a way that maximizes their value. It will take some work on your part, but the security of your data will be far greater.




